BeyondTrust Issues Urgent Patch for Critical Vulnerability in PRA and RS Products – OfficialSarkar
BeyondTrust has disclosed details of a critical security flaw in Privileged Remote Access (PRA) and Remote Support (RS) products that could potentially lead to the execution of arbitrary commands.
Privileged Remote Access controls, manages, and audits privileged accounts and credentials, offering zero trust access to on-premises and cloud resources by internal, external, and third-party users. Remote Support allows service desk personnel to securely connect to remote systems and mobile devices.
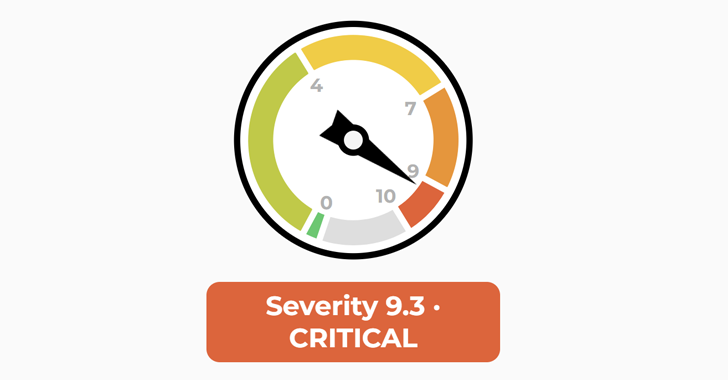
The vulnerability, tracked as CVE-2024-12356 (CVSS score: 9.8), has been described as an instance of command injection.
“A critical vulnerability has been discovered in Privileged Remote Access (PRA) and Remote Support (RS) products which can allow an unauthenticated attacker to inject commands that are run as a site user,” the company said in an advisory.
An attacker could exploit the flaw by sending a malicious client request, effectively leading to the execution of arbitrary operating systems within the context of the site user.
The issue impacts the following versions –
- Privileged Remote Access (versions 24.3.1 and earlier) – Fixed in PRA patch BT24-10-ONPREM1 or BT24-10-ONPREM2
- Remote Support (versions 24.3.1 and earlier) – Fixed in RS patch BT24-10-ONPREM1 or BT24-10-ONPREM2
A patch for the vulnerability has already been applied to cloud instances as of December 16, 2024. Users of on-premise versions of the software are recommended to apply the latest fixes if they are not subscribed to automatic updates.
“If customers are on a version older than 22.1, they will need to upgrade in order to apply this patch,” BeyondTrust said.
The company said the shortcoming was uncovered during an ongoing forensics investigation that was initiated following a “security incident” on December 2, 2024, involving a “limited number of Remote Support SaaS customers.”
“A root cause analysis into a Remote Support SaaS issue identified an API key for Remote Support SaaS had been compromised,” BeyondTrust said, adding it “immediately revoked the API key, notified known impacted customers, and suspended those instances the same day while providing alternative Remote Support SaaS instances for those customers.”
BeyondTrust also said it’s still working to determine the cause and impact of the compromise in partnership with an unnamed “cybersecurity and forensics firm.”
Source: TheHackerNews