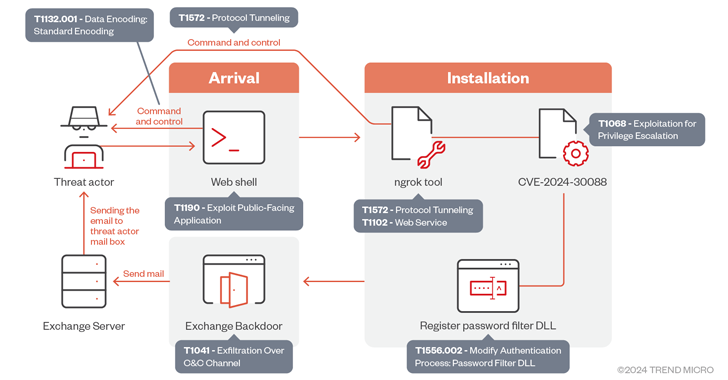
5 Steps to Boost Detection and Response in a Multi-Layered Cloud – OfficialSarkar
Oct 14, 2024The Hacker NewsCloud Security / Vulnerability The link between detection and response (DR) practices and cloud security has historically been weak. As global organizations increasingly adopt cloud environments, security strategies have largely focused on “shift-left” practices—securing code, ensuring proper cloud posture, and fixing misconfigurations. However, this approach has led to an over-reliance on…