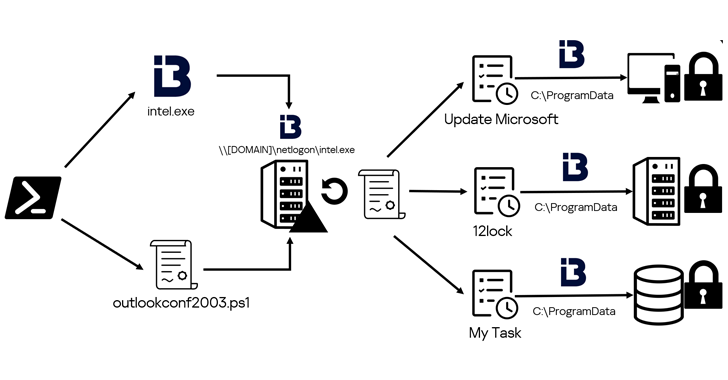
Discover Latest Ransomware Tactics and Zero Trust Strategies in This Expert Webinar – OfficialSarkar
Sep 24, 2024The Hacker NewsWebinar / Cybersecurity Ransomware is no longer just a threat; it’s an entire industry. Cybercriminals are growing more sophisticated, and their tactics are evolving rapidly. This persistent danger is a major concern for business leaders. But there’s good news: you don’t have to be defenseless. What if you could gain a…