One More Tool Will Do It? Reflecting on the CrowdStrike Fallout – OfficialSarkar
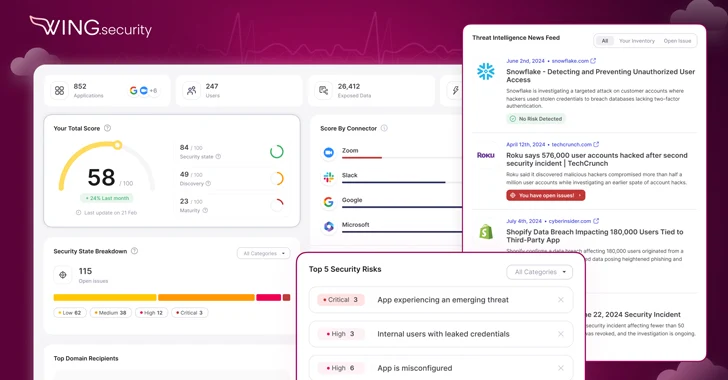
Sep 09, 2024The Hacker NewsData Protection / Threat Detection The proliferation of cybersecurity tools has created an illusion of security. Organizations often believe that by deploying a firewall, antivirus software, intrusion detection systems, identity threat detection and response, and other tools, they are adequately protected. However, this approach not only fails to address the fundamental…