Google Fixes GCP Composer Flaw That Could’ve Led to Remote Code Execution – OfficialSarkar
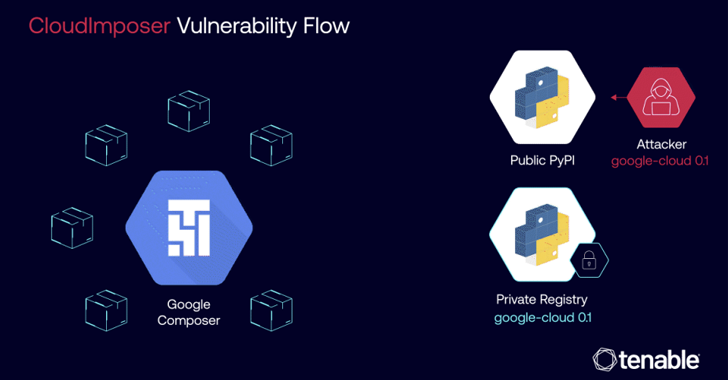
Sep 16, 2024Ravie LakshmananCloud Security / Vulnerability A now-patched critical security flaw impacting Google Cloud Platform (GCP) Composer could have been exploited to achieve remote code execution on cloud servers by means of a supply chain attack technique called dependency confusion. The vulnerability has been codenamed CloudImposer by Tenable Research. “The vulnerability could have allowed…