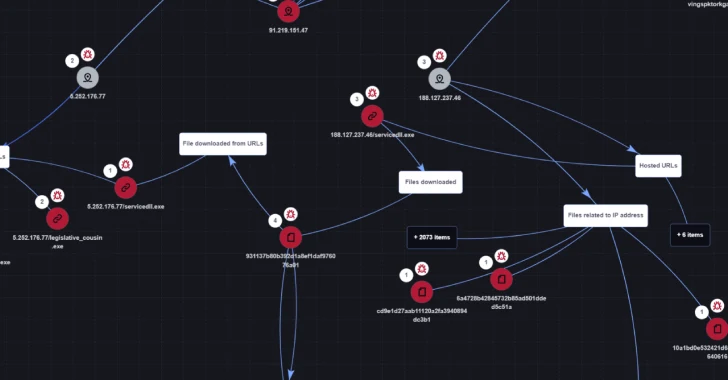
Google Confirms CVE-2024-32896 Exploited in the Wild, Releases Android Security Patch – OfficialSarkar
Sep 04, 2024Ravie LakshmananVulnerability / Mobile Security Google has released its monthly security updates for the Android operating system to address a known security flaw that it said has come under active exploitation in the wild. The high-severity vulnerability, tracked as CVE-2024-32896 (CVSS score: 7.8), relates to a case of privilege escalation in the Android…