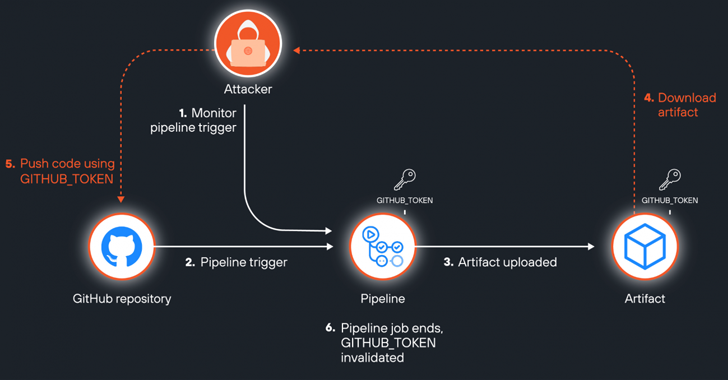
Google Pixel Devices Shipped with Vulnerable App, Leaving Millions at Risk – OfficialSarkar
Aug 16, 2024Ravie LakshmananMobile Security / Software Security A large percentage of Google’s own Pixel devices shipped globally since September 2017 included dormant software that could be used to stage nefarious attacks and deliver various kinds of malware. The issue manifests in the form of a pre-installed Android app called “Showcase.apk” that comes with excessive…