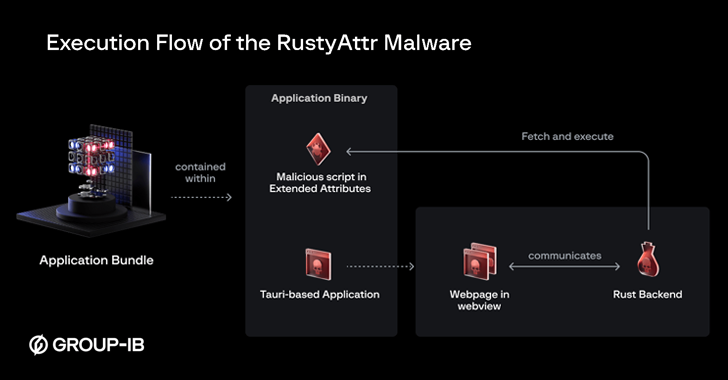
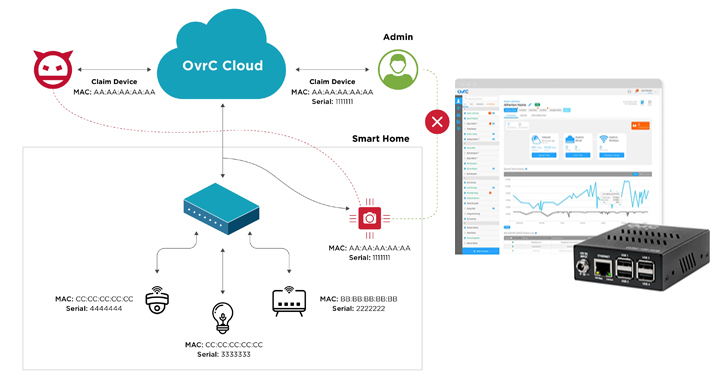
Google Warns of Rising Cloaking Scams, AI-Driven Fraud, and Crypto Schemes – OfficialSarkar
Nov 14, 2024Ravie LakshmananArtificial Intelligence / Cryptocurrency Google has revealed that bad actors are leveraging techniques like landing page cloaking to conduct scams by impersonating legitimate sites. “Cloaking is specifically designed to prevent moderation systems and teams from reviewing policy-violating content which enables them to deploy the scam directly to users,” Laurie Richardson, VP and…