VMware ESXi Flaw Exploited by Ransomware Groups for Admin Access – OfficialSarkar
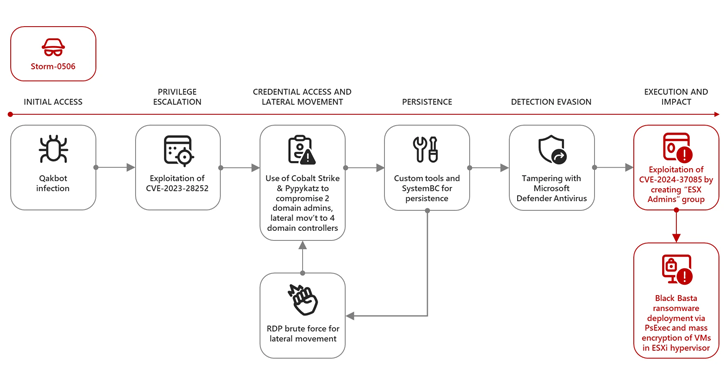
A recently patched security flaw impacting VMware ESXi hypervisors has been actively exploited by “several” ransomware groups to gain elevated permissions and deploy file-encrypting malware. The attacks involve the exploitation of CVE-2024-37085 (CVSS score: 6.8), an Active Directory integration authentication bypass that allows an attacker to obtain administrative access to the host. “A malicious actor…