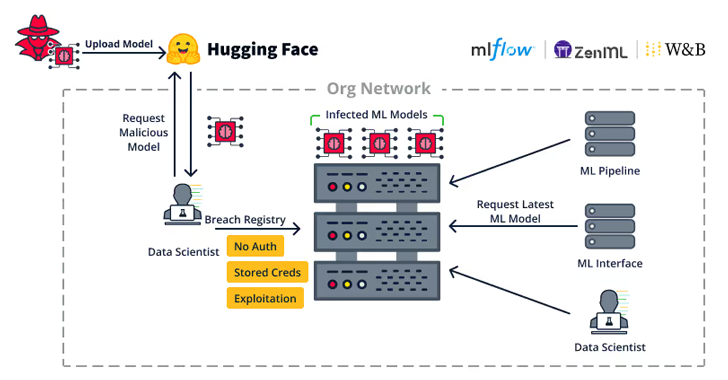
Security Flaws in Popular ML Toolkits Enable Server Hijacks, Privilege Escalation – OfficialSarkar
Nov 11, 2024Ravie LakshmananMachine Learning / Vulnerability Cybersecurity researchers have uncovered nearly two dozen security flaws spanning 15 different machine learning (ML) related open-source projects. These comprise vulnerabilities discovered both on the server- and client-side, software supply chain security firm JFrog said in an analysis published last week. The server-side weaknesses “allow attackers to hijack…