Hackers Use Fake GlobalProtect VPN Software in New WikiLoader Malware Attack – OfficialSarkar
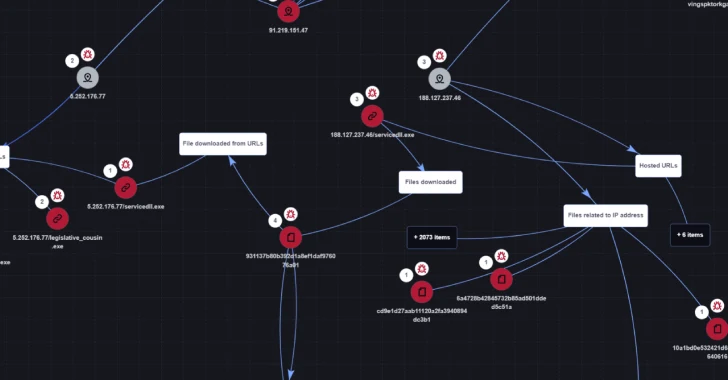
Sep 04, 2024Ravie LakshmananMalware / Network Security A new malware campaign is spoofing Palo Alto Networks’ GlobalProtect VPN software to deliver a variant of the WikiLoader (aka WailingCrab) loader by means of a search engine optimization (SEO) campaign. The malvertising activity, observed in June 2024, is a departure from previously observed tactics wherein the malware…


![Which District of Sikkim has the Lowest Literacy Rate? [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/District-of-Sikkim-with-the-Lowest-Literacy-Rate-768x432.png)
![List of Railway Zones of India and Their Headquarters [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/Railway-Zones-in-India-768x432.png)
![Thulasimathi Murugesan and Manisha Ramadass Shine at Paris 2024 Paralympics [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/Thulasimathi-Murugesan-and-Manisha-Ramadass-Shine-at-Paris-2024-Paralympics-768x432.png)
![World Bank Ups India’s Growth Forecast to 7% for FY25 [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/2023-09-26T234642Z_2039832791_RC2WD0A0C1GI_RTRMADP_3_WORLDBANK-FINANCING-1-768x432.jpg)
![Lord’s to Host the ICC World Test Championship Final in 2025 [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/Lords-to-Host-the-ICC-World-Test-Championship-Final-in-2025-768x432.png)
![Its Overview, History, Objectives and Functions [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/IPG-Full-Form-Its-Overview-History-Objectives-and-Functions-768x432.png)

![West Bengal Assembly Passes Historic Anti-Rape ‘Aparajita’ Bill Amid Political Drama [Current Affairs]](https://officialsarkar.in/wp-content/uploads/2024/09/mamata-west-bengal-assembly-anti-rape-bill-1-768x432.jpg)