Vietnamese Human Rights Group Targeted in Multi-Year Cyberattack by APT32 – OfficialSarkar
A non-profit supporting Vietnamese human rights has been the target of a multi-year campaign designed to deliver a variety of malware on compromised hosts.
Cybersecurity company Huntress attributed the activity to a threat cluster known as APT32, a Vietnamese-aligned hacking crew that’s also known as APT-C-00, Canvas Cyclone (formerly Bismuth), Cobalt Kitty, and OceanLotus. The intrusion is believed to have been ongoing for at least four years.
“This intrusion has a number of overlaps with known techniques used by the threat actor APT32/OceanLotus, and a known target demographic which aligns with APT32/OceanLotus targets,” security researchers Jai Minton and Craig Sweeney said.
OceanLotus, active since at least 2012, has a history of targeting company and government networks in East-Asian countries, particularly Vietnam, the Philippines, Laos, and Cambodia with the end goal of cyber espionage and intellectual property theft.
Attack chains typically make use of spear-phishing lures as the initial penetration vector to deliver backdoors capable of running arbitrary shellcode and collecting sensitive information. That said, the group has also been observed orchestrating watering hole campaigns as early as 2018 to infect site visitors with a reconnaissance payload or harvest their credentials.
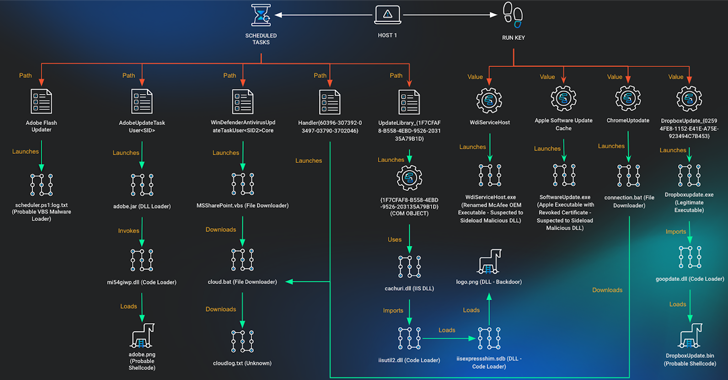
The latest set of attacks pieced together by Huntress spanned four hosts, each of which was compromised to add various scheduled tasks and Windows Registry keys that are responsible for launching Cobalt Strike Beacons, a backdoor that enables the theft of Google Chrome cookies for all user profiles on the system, and loaders responsible for launching embedded DLL payloads.
The development comes as South Korean users are the target of an ongoing campaign that likely leverages spear-phishing and vulnerable Microsoft Exchange servers to deliver reverse shells, backdoors, and VNC malware to gain control of infected machines and steal credentials stored in web browsers.
Source: TheHackerNews