Cybercriminals Exploit Popular Game Engine Godot to Distribute Cross-Platform Malware – OfficialSarkar
A popular open-source game engine called Godot Engine is being misused as part of a new GodLoader malware campaign, infecting over 17,000 systems since at least June 2024.
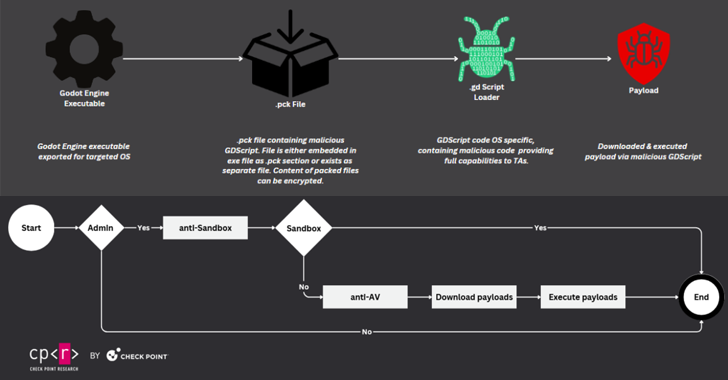
“Cybercriminals have been taking advantage of Godot Engine to execute crafted GDScript code which triggers malicious commands and delivers malware,” Check Point said in a new analysis published Wednesday. “The technique remains undetected by almost all antivirus engines in VirusTotal.”
It’s no surprise that threat actors are constantly on the lookout for new tools and techniques that can help them deliver malware while sidestepping detection by security controls, even as defenders continue to erect new guardrails.
The newest addition is Godot Engine, a game development platform that allows users to design 2D and 3D games across platforms, including Windows, macOS, Linux, Android, iOS, PlayStation, Xbox, Nintendo Switch, and the web.
The multi-platform support also makes it an attractive implement in the hands of adversaries who can now leverage it to target and infect devices at scale, effectively broadening the attack surface.
What makes the campaign stand out is that it leverages the Stargazers Ghost Network – in this case, a set of about 200 GitHub repositories and more than 225 bogus accounts – as a distribution vector for GodLoader.
“These accounts have been starring the malicious repositories that distribute GodLoader, making them appear legitimate and safe,” Check Point said. “The repositories were released in four separate waves, primarily targeting developers, gamers, and general users.”
The attacks, observed on September 12, September 14, September 29, and October 3, 2024, have been found to employ Godot Engine executables, also known as pack (or .PCK) files, to drop the loader malware, which is then responsible for downloading and executing final-stage payloads such as RedLine Stealer and the XMRig cryptocurrency miner from a Bitbucket repository.
In addition, the loader incorporates features to bypass analysis in sandboxed and virtual environments and add the entire C:\ drive to the Microsoft Defender Antivirus exclusions list to prevent the detection of malware.
The cybersecurity company said GodLoader artifacts are primarily geared towards targeting Windows machines, although it noted that it’s trivial to adapt them to infect macOS and Linux systems.
What’s more, while the current set of attacks involves the threat actors building custom Godot Engine executables for malware propagation, it could be taken a notch higher by tampering with a legitimate Godot-built game after obtaining the symmetric encryption key used to extract the .PCK file.
This sort of attack, however, can be averted by switching to an asymmetric-key algorithm (aka public-key cryptography) that relies on a public and private key pair to encrypt/decrypt data.
The malicious campaign serves up another reminder of how threat actors frequently leverage legitimate services and brands to evade security mechanisms, necessitating that users download software only from trusted sources.
“Threat actors have utilized Godot’s scripting capabilities to create custom loaders that remain undetected by many conventional security solutions,” Check Point said. “Since Godot’s architecture allows platform-agnostic payload delivery, attackers can easily deploy malicious code across Windows, Linux, and macOS, sometimes even exploring Android options.”
“Combining a highly targeted distribution method and a discreet, undetected technique has resulted in exceptionally high infection rates. This cross-platform approach enhances malware versatility, giving threat actors a powerful tool that can easily target multiple operating systems. This method allows attackers to deliver malware more effectively across various devices, maximizing their reach and impact.”
Source: TheHackerNews